I still remember the good old days when I would just write “javascript:alert(document.cookie)” in my address bar and the browser would happily show me the JavaScript-accessible cookie values for the current domain. These were simpler days…
Mid-2011 the developers of Firefox decided that allowing the “javascript” directive in the URL bar was being abused by attackers to conduct self-XSS attacks more than it was being used for legitimate purposes. If you are not familiar with self-XSS fear not… they are quite easy to explain.
In short, self-XSS happens when an attacker convinces a user to copy-paste some malicious JavaScript code in his URL bar and hit ‘Enter’. This was used a lot in Facebook, since people there are usually very willing to follow instructions in order to get access to some sort of “video”, or “application” or information about how many people checked-out their profile today. Matt Jones has made a nice video demonstrating the attack which you can check out right here. The effect of this, is exactly the same as an attacker injecting malicious JavaScript by exploiting the usual and well-known XSS bugs (reflected, stored, DOM-based).
Back to Firefox… so Firefox decided to disallow the use of JavaScript in the URL bar. So no more self-XSS right? Wrong! In the newer versions of Firefox, there is a pretty ‘Web console’ which a user can access and type in arbitrary JavaScript that will again run in the context of the current domain.
While people have accepted this, they believe that it is a greater hassle to users who will not do it as easily as they used to do the self-XSS through the browser URL bar. The purpose of this post, is to claim that this is not true.
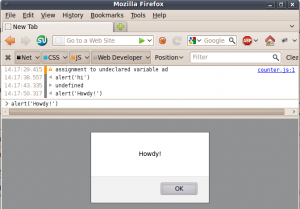
The ‘Web console’ of Firefox has a handy default keyboard shortcut from which it is accessible: Ctrl+Shift+K. Now compare the list of instructions that an attacker would use to conduct self-XSS in the past, and the list of instructions now.
Old:
- Select the following text: javascript:alert('Welcome to a world of pain');
- Hit the following:
-
- Ctrl+C
- Ctrl+L
- Ctrl+V
- Enter
New (you can actually follow along):
- Select the following text: alert('Welcome to a world of pain');
- Hit the following:
-
- Ctrl+C
- Ctrl+L
- Ctrl+Shift+K
- Ctrl+V
- Enter
The only extra action needed to perform the attack is the Ctrl+Shift+K between the selection of the location bar (Ctrl+L) and the pasting of code (Ctrl+V). If anything I would claim that this is a smoother attack because the word “javascript” doesn’t need to be written as part of the malicious vector since the Web Console expects JavaScript and thus doesn’t need to be told: “Interpret the rest as JavaScript”.
In short I don’t believe that this is a step in the right direction. Call me pessimistic but executing an extra step as part of getting access to “Virtual Carrots” or “Hot girls” doesn’t look like it would stop the kind of people that would fall for this attack in the first place.
Nick Nikiforakis
P.S. Happy New Year! 🙂


4 Responses to Firefox and Self-XSS