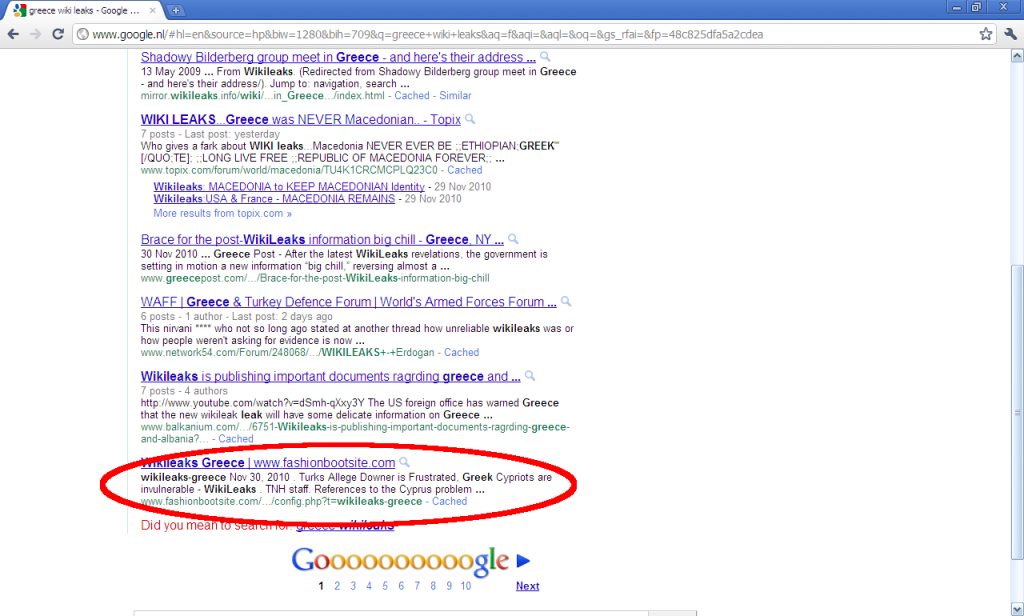
While I was in Eindhoven for OWASP BeNeLux 2010 I was at some point searching online for WikiLeaks posts regarding greek politics. I was checking the results from the first page of Google when suddenly this caught my eye:
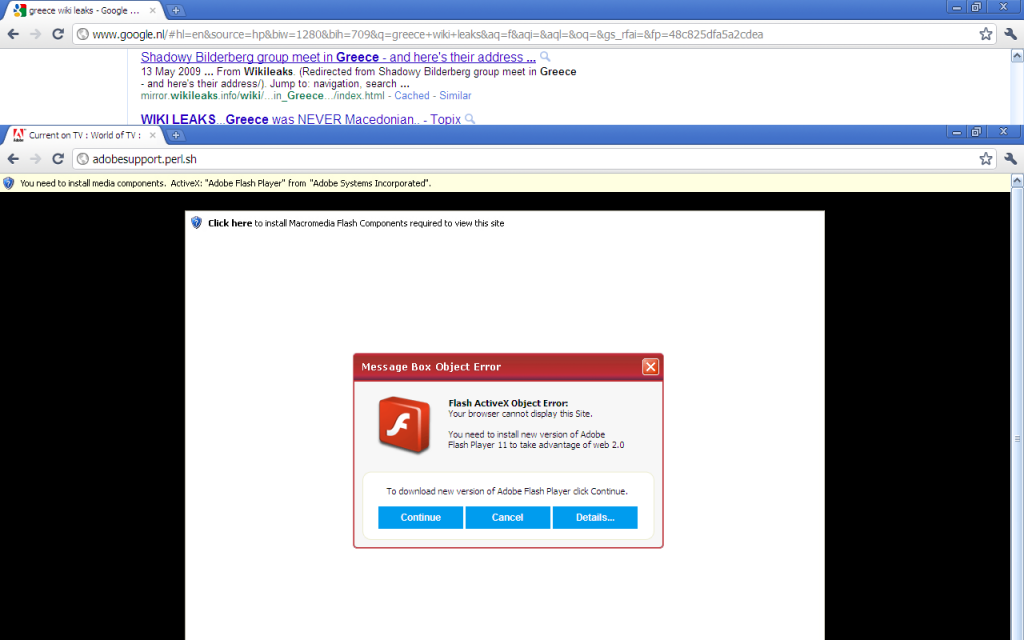
What can a fashion website about boots have in common with “Wikileaks Greece”? The answer is nothing. It has been hacked and the attacker has uploaded config.php file which serves a double purpose:
- When Google crawls it, the website appears to have all sorts of legitimate and interesting content. This way, the site is added and will be presented to users who search for that content; in our case wikileaks stories about Greece.
- When a user who isn’t Google clicks on the link (the page can recognise that using the User-Agent, the IP address or the domain of the user) then the user is redirected to something else.
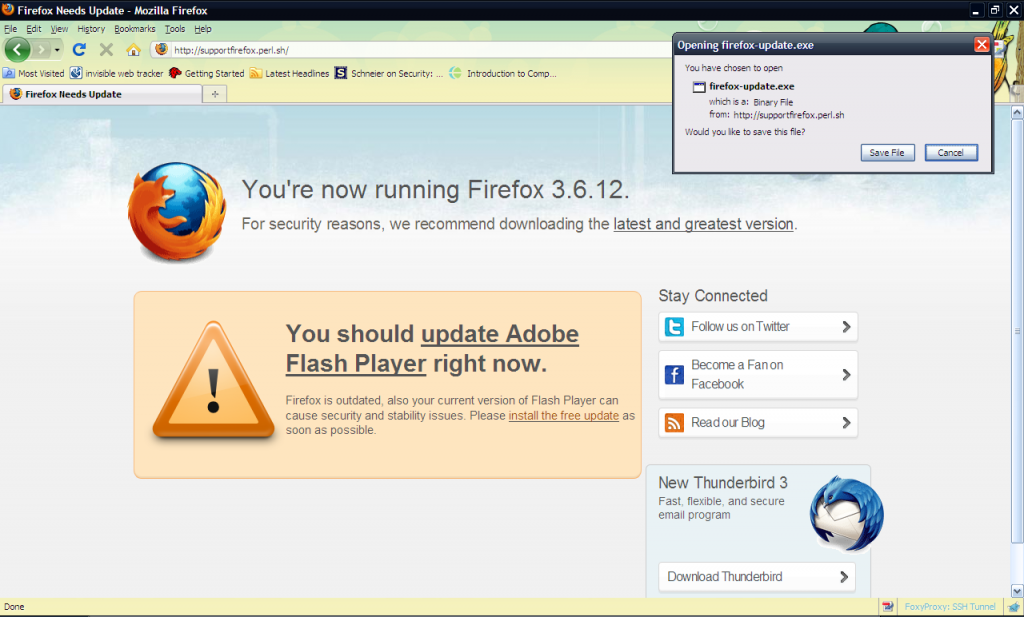
You can all at this point guess what would happen if I clicked continue. Download->Execute->Be infected. That’s not really news to anyone in the security community anymore. I decided however to give the website a try, using instead of Google Chrome, Mozilla Firefox. This is what I got:
Now, what does this remind you of? Anyone? I will gladly tell you… Mozilla Firefox actually used the very same page to “warn” their users when they were using certain versions of Adobe Flash Player that were vulnerable to remote code injection attacks. Now pause and think… Mozilla is training their users to believe what they see in their browsers and take action on it. At the same time, the security community is trying to make people understand that they must NOT trust websites.
In parenting this is called “inconsistency”. If you want your child to learn a certain behaviour, e.g., that hitting other children is not allowed, you must always be consistent about it. Whenever he does it, the child must be scolded/punished or else it will be confused and act in random ways.
In the same way, the security community must choose a way and stick to it, if they ever want to educate people about safe computer use. Non-security people can’t be blamed of being “stupid” when these things happen…
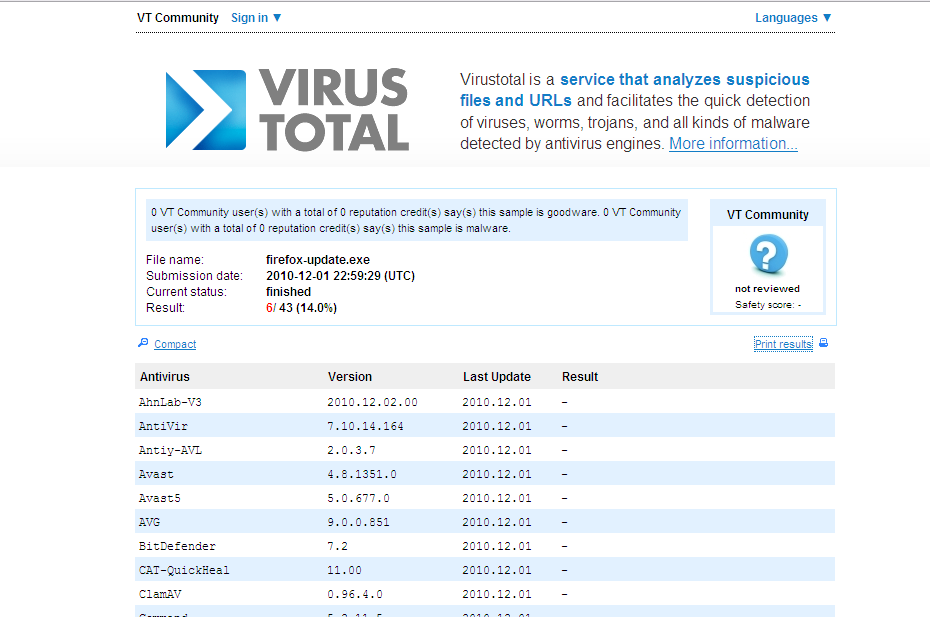
As a closing thought, I want to say that all the things that Antivirus companies say about “pro-active” security is just baloney. They work with signature matching and that’s that… Anyone interested in how our “firefox-update.exe” scored?

One Response to Security inconsistencies…