Did you know that if you use a popular cheap web hosting product and you haven’t changed the default error pages of your sites, you are most likely hosting an open redirect? If not, read on 🙂
Suppose for a second that you are a loyal customer of babyhow.com, an eshop selling stuff for your baby. One beautiful day you receive an email letting you know that babyhow.com has moved its business and providing you with a link to read more:
http://www.babyhow.com/We_Have_Moved?%27%7d%3b%7d%74%6f%70%2e%6c %6f%63%61%74%69%6f%6e%2e%72%65%70%6c%61%63%65%28%27%68%74%74%70 %3a%2f%2f%77%77%77%2e%63%6e%6e%2e%63%6f%6d%27%29%3b%66%75%6e%63 %74%69%6f%6e%20%64%75%6d%6d%79%28%29%7b%76%61%72%20%66%6f%6f%3d %7b%31%3a%27%31%a
If you’ve read more posts from my blog you already know that the fact that I am hiding something from you by turning it into hex isn’t a good sign. But suppose, that you don’t know that. You click on that link, expecting to read more (copy-paste the thing and try it…its fun, I promise 🙂 ). For a second you see the banner of “Bluehost.com”, a cheap shared hosting business which claims to host “millions of domains”. A second later however, you are suddenly at the main page of cnn.com. What happened? Welcome to the world of open redirects… with a twist.
Open redirects
According to OWASP, an open redirect is “an application that takes a parameter and redirects a user to the parameter value without any validation. This vulnerability is used in phishing attacks to get users to visit malicious sites without realizing it.”
Sounds dangerous, doesn’t it? Now you may think… these stupid people at babyhow.com should fix their stuff. But you’d be wrong. Babyhow.com doesn’t have an open redirect. Its their hosting provider that has!
Ads instead of errors
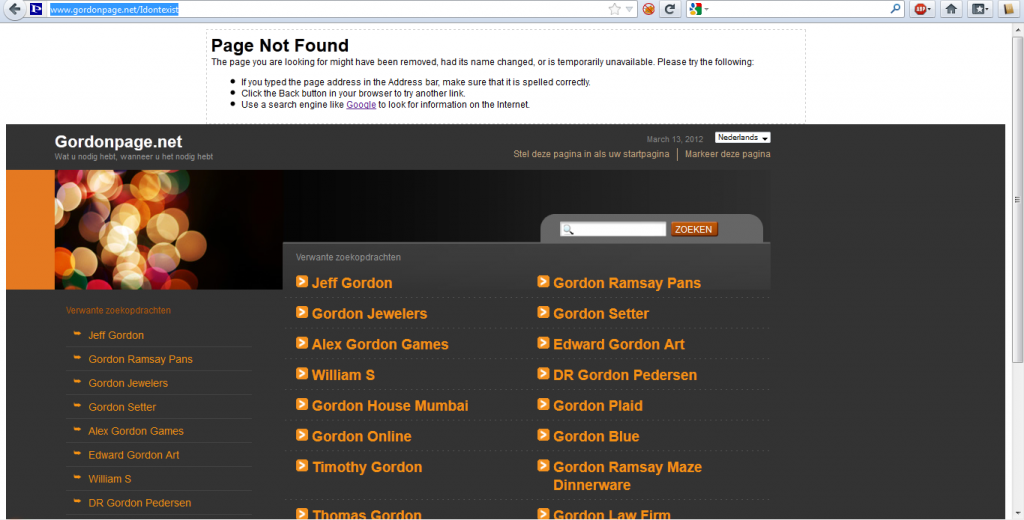
I recently realized that the majority of the cheap and popular shared hosting companies (verified on bluehost.com and fatcow.com) are a bit sneakier than they should be. By default, when you host a website on their servers and a user requests a page that doesn’t exist, instead of sending a vanilla 404 message, they decide to capitalize on the opportunity and serve some ads while they’re at it. Look what happens when I ask for http://www.gordonpage.net/i_dont_exist, a domain hosted on fatcow.com and a non-existent page:
I am pretty sure that Mr. Page doesn’t know that his site is serving random ads. If he did, he would have disabled this default behavior. To add insult to injury, the script responsible for creating the iframe that displays the ads, uses the URL of the error page in an insecure way, allowing an attacker to inject arbitrary JavaScript code. The only downside is that the injected code runs within the iframe and thus you can’t access resources of the site (like session cookies). What you can do however, is redirect the whole browser to a destination of your choice. In my earlier example, the injected code was redirecting the user from babyhow.com to cnn.com, but think in terms of phishing credentials or brand wars and you get the point 🙂 Here’s the link that I showed you earlier without the use of hex:
http://babyhow.com/We_Have_Moved?'};}top.location.replace('http://
www.cnn.com');function dummy(){var foo={1:'1
Big picture:
If you are using a cheap shared hosting provider and haven’t changed the default way of responding to 404 messages, your site is most likely “hosting” an open redirect that can damage both your business and your users. The sad thing is that it isn’t even your fault… its your hosting provider’s fault that tries to squeeze every last penny out of you and your visitors.
Till next time
Nick Nikiforakis